Picture this: You’re in the middle of dinner with friends when your work phone buzzes. It’s the fraud supervisor with alarming news: Low-value transactions are suddenly flooding your servers. Your gut tightens as you hastily excuse yourself and head straight to the office to help secure your customers’ accounts against what turns out to be a Bank Identification Number (BIN) attack.
The lowdown on BIN attacks
In these types of increasingly common fraud attacks, criminals, often aided by artificial intelligence (AI), attempt to generate legitimate credit card numbers by starting with a known BIN. Comprising the first six or eight digits of a payment card, a BIN identifies the issuing bank and can also reveal other card characteristics such as type, tier, or geographic region.
The speed and effectiveness of BIN attacks has been drastically enhanced by AI-powered bots that generate credit card numbers along with related information like expiration dates and CVV codes. When viable card numbers are identified, the bots proceed to test the card by making small purchases. The fraudsters then make larger purchases until the account is flagged and frozen by the cardholder or financial institution.
BIN attacks are difficult for traditional fraud solutions to detect because they are designed to blend in with normal transaction behavior. By running tests across thousands of websites and other online payment gateways, and spreading their attempts across many targets, they can avoid rate limits and velocity checks. Since each transaction looks benign in isolation, most traditional rule-based systems fail to recognize broader attack patterns.

From the shadows to center stage
A major factor fueling the global increase in fraud is the emergence of Fraud-as-a-Service (FaaS), a shadow economy where cybercriminals provide illicit tools, resources, and support systems to others for a fee. Mimicking the structure of a legitimate business, FaaS operations often provide around-the-clock customer service, detailed guides, and even satisfaction guarantees.
FaaS enables individuals with little to no technical background to carry out BIN attacks at scale by scanning thousands of websites simultaneously for security weaknesses and exploiting any vulnerabilities they uncover. As a result, global BIN attacks have soared, with incidents increasing by 80 percent since 2020. As e-commerce continues its rapid global expansion, fraud is rising just as quickly. Recent data highlights the alarming scale of the problem: online payment fraud in e-commerce resulted in $48 billion in losses in 2024, Juniper Research reports, with cumulative global losses projected to surpass $343 billion between 2024 and 2027.
Collateral damage: BIN attacks are costing banks and payment processors billions
The fallout from BIN attacks goes far beyond individual transactions. The global financial sector has incurred more than $12 billion in direct losses due to reported cyber incidents that affect the following aspects of business performance and sustainability.
Rising chargebacks: When fraudsters test card numbers on e-commerce sites, any resulting unauthorized transactions are often disputed by cardholders. If the dispute is successful, the payment is reversed, and in many cases, merchants are the ones left covering the cost of both the chargeback and dispute resolution efforts.
Reputation damage: Being linked to fraudulent activity can erode trust in a business. When customers spot unauthorized transactions on their statements associated with a particular merchant, it can create lasting negative perceptions. Banks are particularly vulnerable to reputational harm, especially if they’re seen as lacking sufficient fraud prevention measures.
Regulatory penalties: Banks and payment processors that fail to implement strong safeguards against BIN attacks may face consequences from regulators. This could include fines or even the suspension of operating licenses, particularly for payment processors that are expected to meet strict compliance standards.
Damaged partnerships: BIN attacks can also strain or sever a bank’s relationships with key partners. For example, if a financial institution identifies a merchant as a frequent target for card testing, it may decide to cut ties with that business to protect its own customers and brand. Likewise, frequent fraudulent transactions linked to a particular payment processor may cause financial institutions to seek transactional services elsewhere.
High-profile BIN attacks that shook the industry
March 2024: A flood of fraudulent transactions were charged to credit card holders at Alabama’s largest credit union, Redstone Federal, via Walmart.com. At the time, Redstone stated that all fraudulent charges would be reversed either by Walmart or reimbursed by the credit union.
January 2018: The U.K.’s Financial Conduct Authority fined Tesco Bank £16.4 million ($21.8 million USD) for failing to “exercise due skill, care and diligence” in protecting its personal account holders against a 2016 BIN attack that resulted in losses of around £2.5 million ($3.3 million USD).
Building proactive strategies to outsmart BIN attacks
BIN attacks are often fast, subtle, and highly automated. By understanding common patterns and combining transaction and behavioral monitoring with strong user verification, organizations can more effectively identify and stop this form of fraud before major damage occurs.
While cardholders and banks can’t prevent criminals from attempting to guess card numbers using known BINs, there are ways to detect and block the resulting fraudulent activity. Although some organizations still rely on manual methods, many are now adopting smarter, more proactive strategies to protect themselves, their partners, and customers. These include:
Limit checkout attempts and use AVS: BIN attacks often involve numerous low-value transactions in quick succession. Limiting the number of checkout attempts per user, especially when paired with incomplete or mismatched address data, can flag or block suspicious activity. Implementing an Address Verification System (AVS) helps catch the mismatched postal codes and street addresses often used in fraudulent attempts.
Monitor transaction patterns: Frequent small transactions, recurring expiration dates, or repeated CVV errors from the same card can all indicate card testing. Monitoring for these patterns allows fraud teams to catch fraudsters before they escalate to higher-value purchases.
Analyze non-transaction events: Fraud isn’t always visible in transactions alone. Monitoring user behavior, such as unusual login attempts, device changes, or IP anomalies, can reveal early warning signs. By flagging these irregularities, businesses can act before the fraud escalates.
Strengthen authentication: Adding an extra layer of user verification, such as CAPTCHA, helps prevent bots from testing stolen or generated card data. Advanced tools like biometric or facial recognition can further reduce the likelihood of unauthorized transactions.
How INETCO BullzAI stops BIN attacks in their tracks
This stealthy form of fraud can be challenging to catch and stop as it unfolds. Because these attacks often follow predictable patterns, it’s essential for risk and fraud teams to recognize both transactional and behavioral warning signs.
With a clear understanding of how BIN attacks operate, teams can create effective detection rules and implement real-time safeguards to block suspicious activity before it escalates.
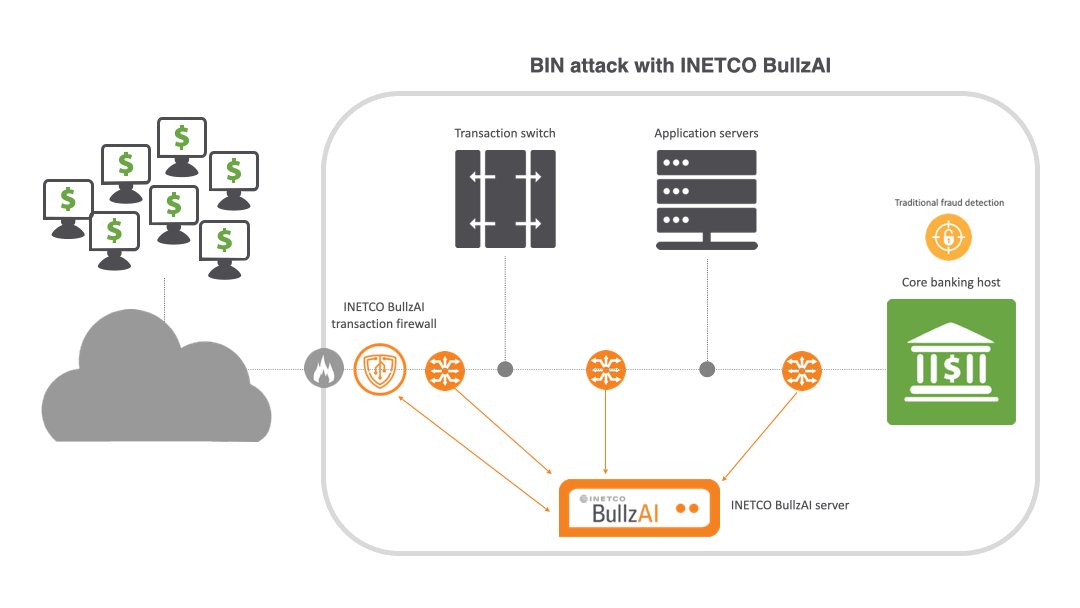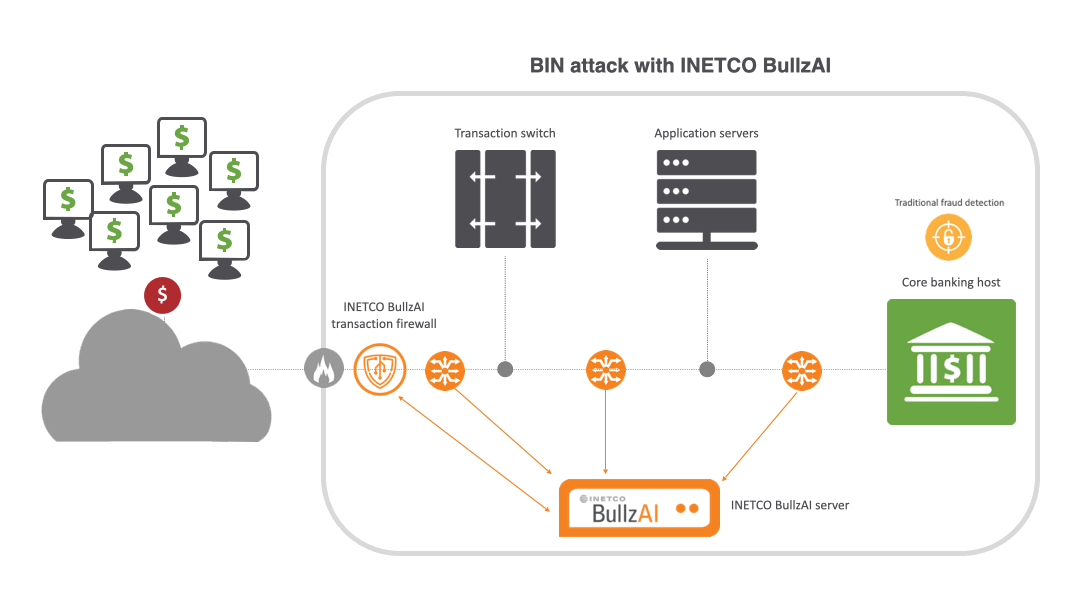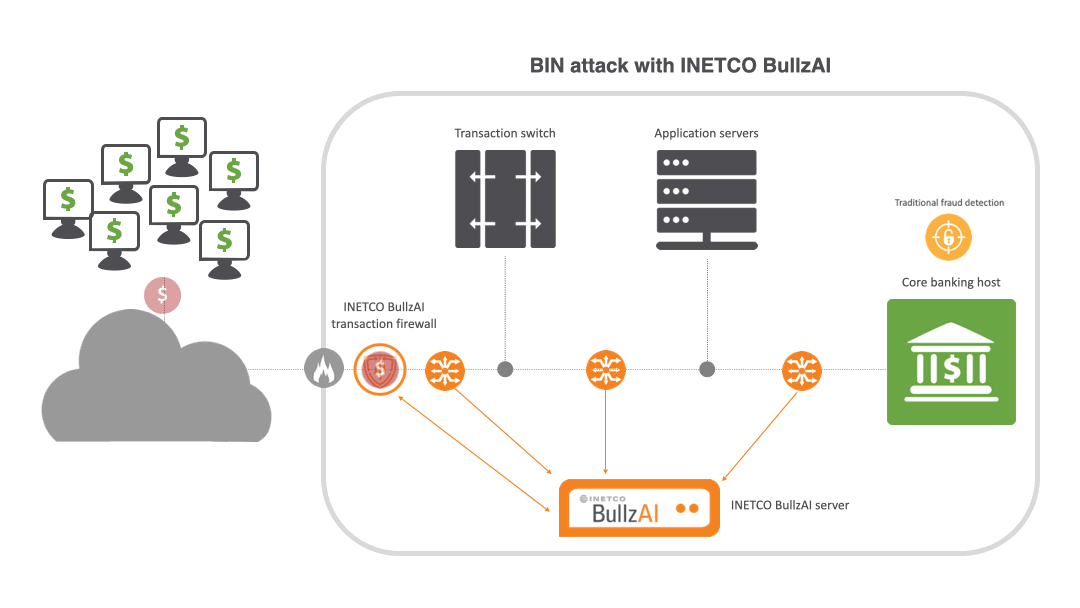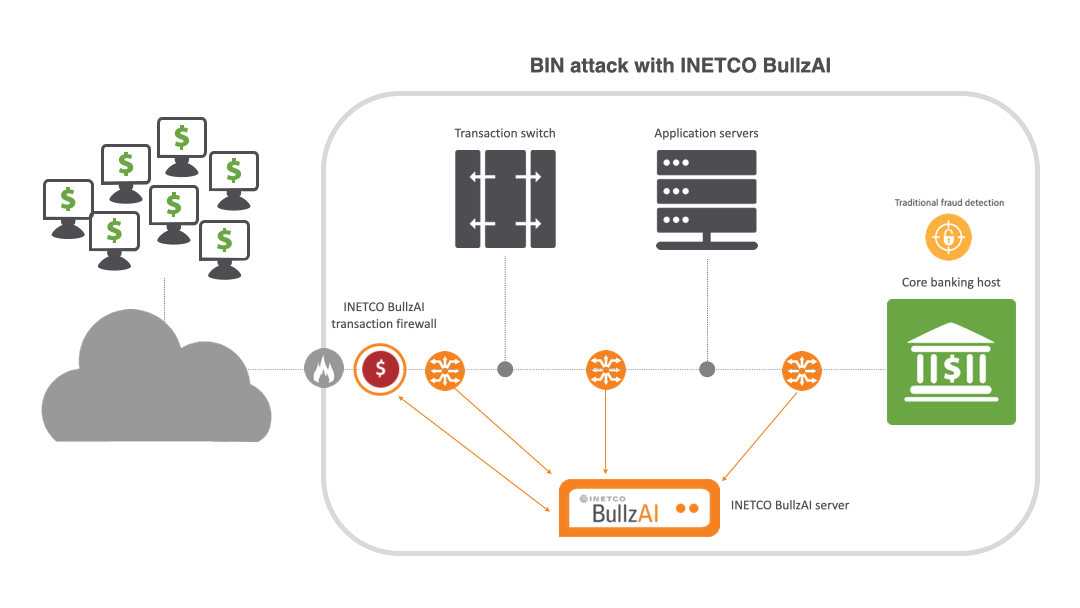
That’s where INETCO BullzAI is playing a vital role for banks and payment processors around the world. INETCO BullzAI is an AI-driven solution that ensures end-to-end transaction protection without compromising the customer experience. It instantly assesses the risk presented by every customer, device and payment using real-time monitoring, adaptive machine learning and behavioral analysis. This empowers banks and payment processors to proactively outsmart fraudsters, stay compliant and stop payment fraud and cyber threats before they disrupt the customer experience.
Unlike other solutions that either struggle to identify attacks or rely on wide-ranging IP blocking to stop them, INETCO BullzAI’s patented transaction firewall identifies card-testing behavior by singling out the devices carrying out the attack and individually blocks them from the transaction network without impacting legitimate customers.
The transaction firewall uses self-learning models to spot behavior deviations for individual users, cards, ATM/POS terminals and mobile devices. It then inspects key data details within each end-to-end transaction, such as terminal IDs and machine fingerprints, to block BIN attacks before they cause harm. This gives financial institutions unparalleled visibility within payment ecosystems to block BIN attacks in real time with surgical accuracy.
No other solution can identify and stop BIN attacks by blocking individual devices. Other solutions force banks and payment processors to carry out a cost-benefit analysis to determine whether they will lose more revenue by shutting down legitimate transactions, or lose more to fraud by allowing the attack to complete.
Discover how the INETCO BullzAI transaction firewall can help you block BIN attacks before they impact your customers. Watch the 3-minute video.
