Picture this: Your payment network appears to be running smoothly, yet subtle inconsistencies in transaction data start to emerge. Authorizations are delayed or altered, and some backend calls never trigger. This isn’t just another case of stolen credentials or card fraud — it’s a devastating man-in-the-middle (MITM) attack that has been going on for months.
How MITM attacks put payments at risk
In this type of “on-path attack,” a criminal inserts themselves between two unsuspecting parties, such as a user and an application. By eavesdropping or impersonating one of the parties, the criminal infiltrates exchanges of information while making it appear as if a normal interaction is taking place.
The main objective is to surreptitiously collect sensitive data — usernames, passwords, banking details and so on — that criminals can use to impersonate victims and solicit funds or additional information to be used for social engineering attacks, identity theft, and fraud.
MITM attacks are widespread in the financial industry. By breaching a bank or payment processor, criminals can manipulate fraud detection controls, modify customer accounts to intercept emails with bank details, and initiate ATM cash-out and jackpotting attacks. For example, in a MITM attack for ATM cash-out, malware is placed on the transaction switch, enabling the creation of cloned cards distributed to money mules. Once the switch is compromised and the malware is activated, the transaction switch goes into a stand-in mode and starts to approve the fraudulent transactions across a large number of ATMs. Threat actors can also silently intercept information sent between two parties and reroute it to phishing sites, and easily encrypt malware into the connection.
MITM attacks thrive on stealth and can be difficult to detect unless transaction message fields are correlated across the upstream and downstream links along a transaction journey. Since initial transactions may still “succeed,” fraud systems relying on backend authorization logs and lacking end-to-end transaction visibility often miss the interception layer, message routing tweaks and link mismatches entirely. And because malicious actors disguise themselves as the endpoint in a line of communication, it’s challenging to spot them.
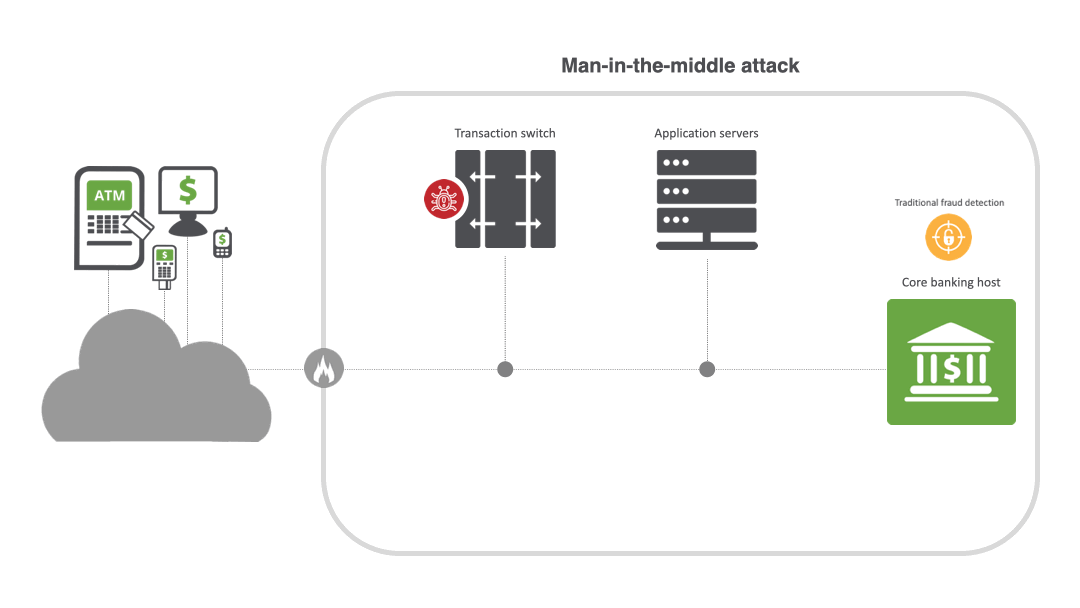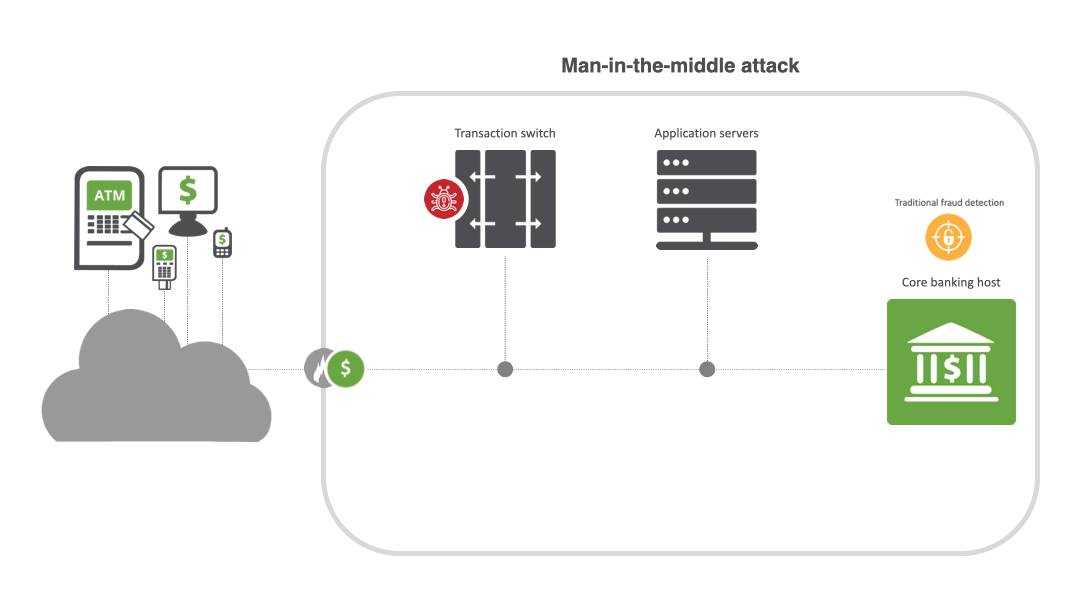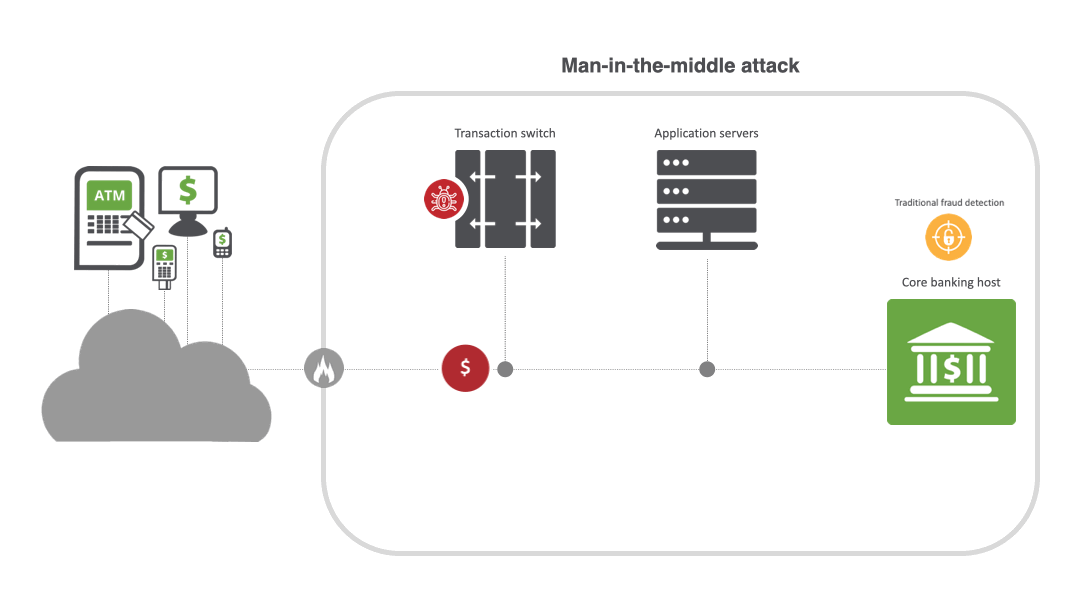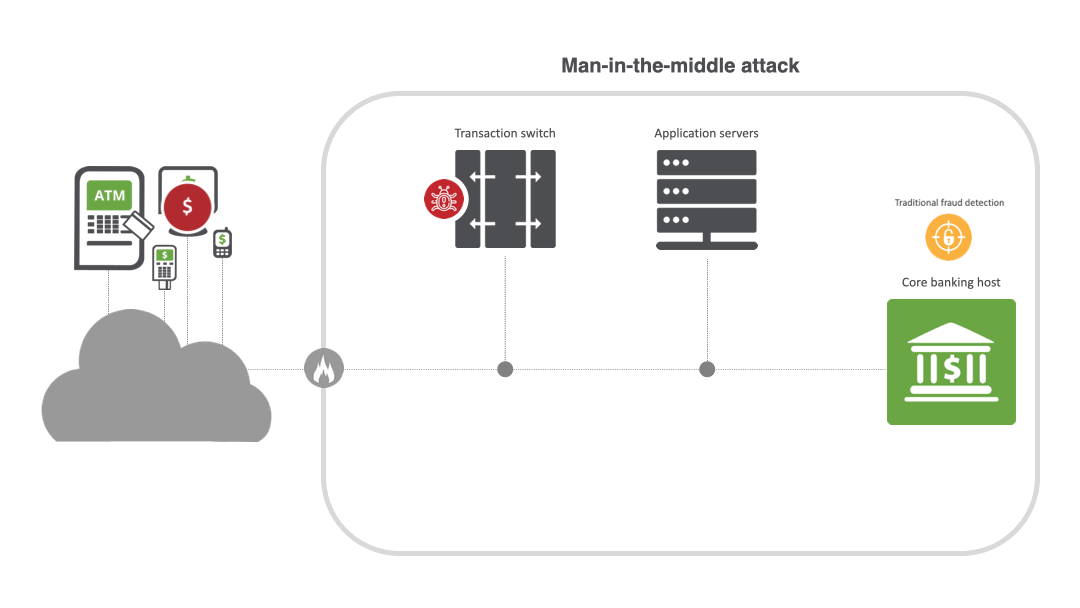
MITM techniques and types
The following four methods account for the lion’s share of MITM fraud:
SL/TLS interception and stripping: This involves downgrading HTTPS or spoofing certificates to steal data via fake “secure” sessions.
Host, DNS or ARP spoofing: This happens when traffic is redirected to attacker-controlled proxies by altering IP or MAC addresses to appear as the legitimate host, enabling eavesdropping on otherwise secure sessions. ATM jackpotting is a popular attack involving remotely installed malware that impersonates the host banking system and authorizes fake transactions, leading to ATMs dispensing cash without debiting the user’s account.
Man-in-the-browser (MITB): These incidents occur when browser-embedded malware intercepts and modifies transactions in real time.
Network relay hijacking: In this scenario, malware or rogue devices placed in the transaction path hijack communication sessions before backend authorizations occur, bypassing fraud systems. One of the most sophisticated ATM attacks — relay attacks — intercept and forward legitimate transaction data that’s unknowingly transmitted via a relay device from a victim with an NFC-enabled card or mobile wallet back to a remote fraudster. A proxy device at an ATM relays the data, bypassing security measures. The ATM authenticates the transaction, allowing cash withdrawals as if the victim were physically present.
Common MITM attack types, meanwhile, include:
Email hijacking: Here, cybercriminals take control of the email accounts of a business or organization. MITM attackers often target financial institutions such as banks or credit card companies for this type of attack. The hackers monitor communications, collect personal data and gather intelligence on transactions. In some cases, they spoof a company email address to convince customers or partners to make deposits or transfer funds into a fraudulent account.
Session hijacking: When a user’s web browser communicates with a website, it temporarily stores information on a session cookie. MITM attackers gain access to these cookies and use them to impersonate a user, or to steal info such as passwords, credit card numbers and other account details.
Wi-Fi eavesdropping: MITM attackers sometimes create public Wi-Fi networks and hot spots in popular public places such as airports and coffee shops. The names of these fraudulent networks are often similar to nearby businesses or other trusted public Wi-Fi connections. Hackers can also compromise legitimate public Wi-Fi hot spots used by the public.
In either case, when unsuspecting users log on, the attackers collect sensitive data such as credit card numbers, usernames, and passwords.
Physical: Physical MITM attacks on ATMs can involve black-box attacks, where a pre-programmed device is connected to the ATM network or cash dispenser to issue unauthorized commands for dispensing cash. Shimming is another example, which involves inserting a shim into a card reader to intercept and capture data from the EMV chip when a legitimate card is used.
One recently uncovered MITM technique has been linked to a TrickBot component known as shaDll. This module worked by planting counterfeit SSL certificates on compromised machines, giving attackers the ability to infiltrate victim networks. Once inside, the tool could reroute online traffic, insert malicious code, capture screenshots, and harvest sensitive information.
What set this incident apart was the apparent partnership between two prominent cybercrime outfits: LUNAR SPIDER and WIZARD SPIDER. The attack leveraged LUNAR SPIDER’s BokBot proxy framework as its base and then incorporated WIZARD SPIDER’s TrickBot capabilities to execute the operation. This suspected collaboration illustrates the increasing sophistication of MITM campaigns and underscores the importance of heightened vigilance against such evolving threats.
MITM attacks: From hidden to the headlines
The rise of digital banking and online transactions has made it easier for hackers to hide on enterprise networks. In addition to a wider attack surface, advanced methods like reverse proxy phishing can bypass traditional defenses like multi-factor authentication, making banking systems more vulnerable. At the same time, contactless and mobile payments have exposed numerous weak points, from public Wi‑Fi to internal switch networks.
The growing prevalence of Fraud‑as‑a‑Service (FaaS), meanwhile, has democratized MITM attacks. Easy-to-deploy fraud kits and pre-configured terminals are now readily available for purchase on dark web marketplaces, enabling even inexperienced criminals to deploy MITM attacks with little technical skill.
High-profile incidents of MITM fraud
2025 — Indian bank blindsided: A critical security flaw was discovered in the YONO SBI: Banking & Lifestyle app, potentially exposing millions of users to MITM attacks and putting sensitive financial data at risk. Developed by the State Bank of India, the app serves as a digital banking platform for one of the world’s largest user bases.
2024 — Tesla tricked: Security researchers revealed that a vulnerability in Tesla’s systems could be exploited for a MITM attack to unlock and steal vehicles. By setting up a spoofed Wi-Fi hotspot at a Tesla charging station, attackers could capture a vehicle owner’s login details. With these credentials, they could register a new “phone key,” giving them unauthorized access to unlock and start the car without the owner’s knowledge.
2017 — Equifax exposed: After the credit reporting giant fell victim to a critical security flaw that exposed the personal data of more than 150 million people — resulting in a settlement totalling more than $580 million USD — the company took down its mobile apps from Apple’s App Store and Google Play because they were discovered to be vulnerable to MITM attacks.
The fallout from MITM attacks
With MITM incidents accounting for 19 percent of successful cyberattacks, the findings of IBM’s most recent “Cost of a Data Breach” report are especially alarming:
- The global average cost of a data breach increased to $4.88 million in 2024, up 10 percent from 2023.
- 46 percent of 2024 data breaches involved customer personal data, which can include tax ID numbers, emails, phone numbers and home addresses.
- The mean time it took defenders to identify and contain a breach was 258 days.
Beyond stolen card and personal financial data, the ripple effects of MITM attacks are severe:
Escalating operational costs: Investigation, reimbursements, chargeback settlements, and internal forensics eat into margins. According to the IBM report, 2024 costs from lost business and post-breach response rose nearly 11 percent over the previous year.
Regulatory risk: Stiff fines can result from failing to comply with Payment Card Industry Data Security Standard (PCI DSS) mandates for end-to-end encryption and intrusion detection.
Eroded trust: Consumers and partners lose confidence when MITM attack chains surface long after they are launched.
Building proactive strategies to beat MITM attacks
Prevention begins with awareness and a layered defense that includes:
Robust multi-factor authentication (MFA) measures: A critical step in preventing MITM attacks is securing all communication channels from end to end. This involves implementing strong MFA protocols to protect access points, and reinforcing these measures with a comprehensive monitoring and detection solution. Importantly, this approach should not be limited to customer-facing services, but should also extend across all internal systems and applications.
Implement advanced threat monitoring and detection solutions: Maintaining full visibility of your infrastructure is essential for spotting unusual activity. Real-time monitoring, coupled with automated alerts and predefined security rules, allows organizations to detect and respond quickly to suspicious behavior. These controls are just as vital within internal networks, where insider threats can pose significant risks.
Security AI and automation: AI-driven and automated security tools are shortening the time required to detect and contain breaches, as well as minimizing the damage they cause. In contrast, organizations that rely solely on manual processes typically face longer response times and higher costs when managing security incidents compared to those leveraging AI and automation. Indeed, according to the IBM report, leveraging AI and automation lowers breach costs by an average of $2.2 million.
Use encrypted Virtual Private Networks (VPNs): Employees should always connect to corporate systems through a VPN. VPNs encrypt internet traffic and hide IP addresses, making it significantly more challenging for attackers to intercept or manipulate data during transmission. While a VPN doesn’t guarantee immunity from MITM attacks, strong encryption protocols add an important layer of defense.
Invest in ongoing employee training: Human error remains one of the most common causes of security breaches. Regular cybersecurity awareness training can help employees recognize phishing attempts, social engineering tactics, and insecure sites. Encouraging staff to verify HTTPS connections ensures that intercepted data remains unreadable to attackers. Also, educating employees on the risks of public Wi-Fi networks and the importance of selecting strong passwords that can change on a regular basis helps strengthen overall organizational security posture.
How INETCO BullzAI shields payments from MITM attacks
INETCO BullzAI delivers a powerful, independent layer of protection by providing multi-point monitoring and correlation across every link of the end-to-end transaction journey. Raw network packets are passively captured from multiple points across the network, and reassembled into complete transactions in real-time. With clear visibility into all the transaction message fields and all the links that make up the transaction authorization journey, you can pinpoint potential attack vectors and instantly detect:
- Anomalies such as missing links and “fake processing”
- Unexpected stand-in modes and fallbacks
- High volume card usage or repeat terminal usage. Coupled with transactional behavior modeling and a patented AI-driven transaction firewall, INETCO BullzAI blocks suspicious transaction activity in milliseconds, whether it is injected, contains altered message content, or has gained approval without ever reaching the core banking host.
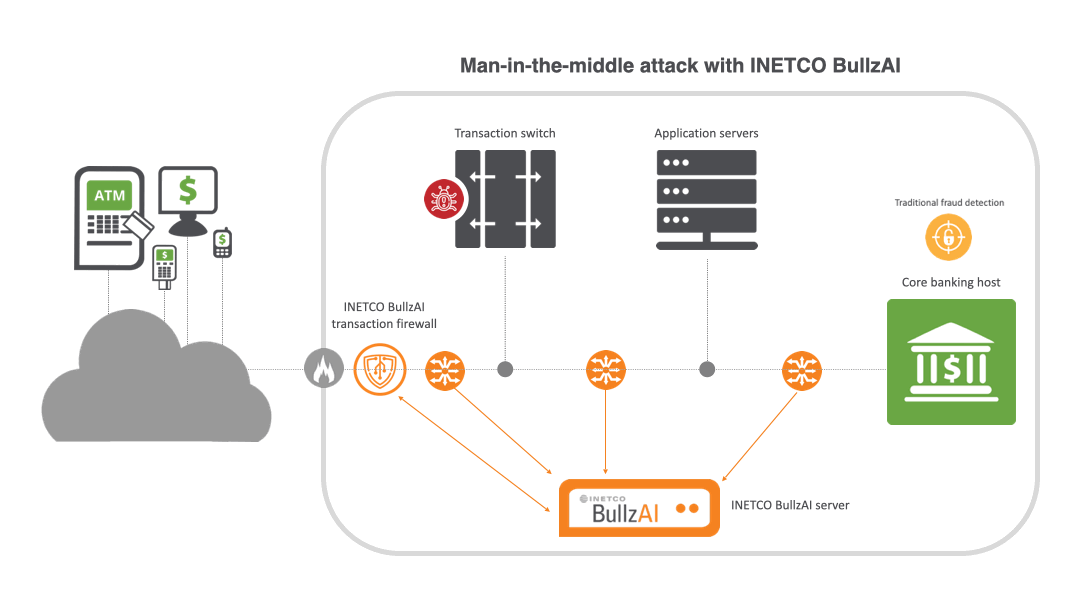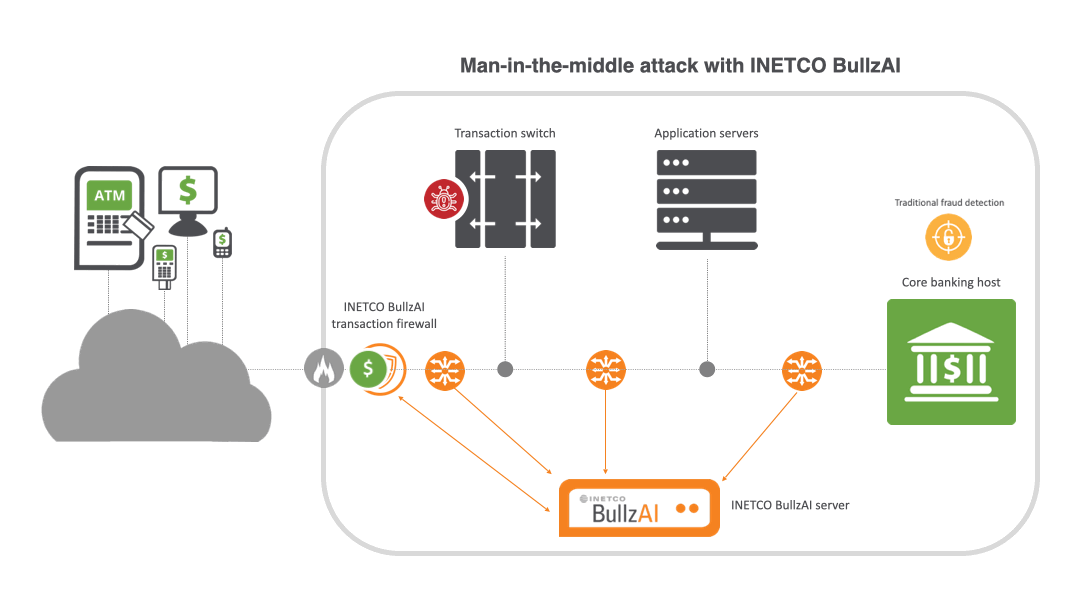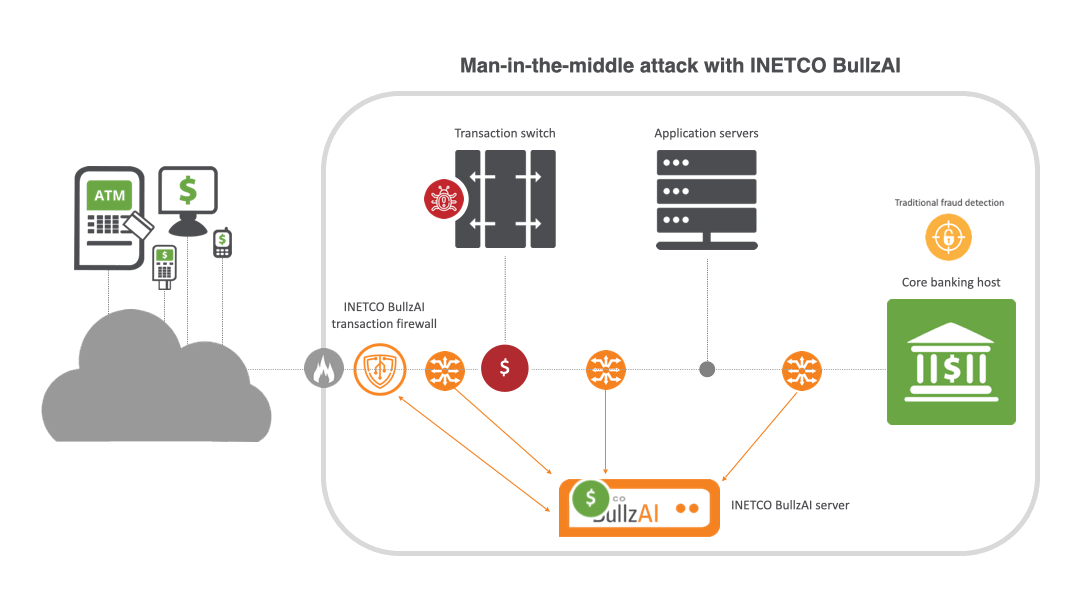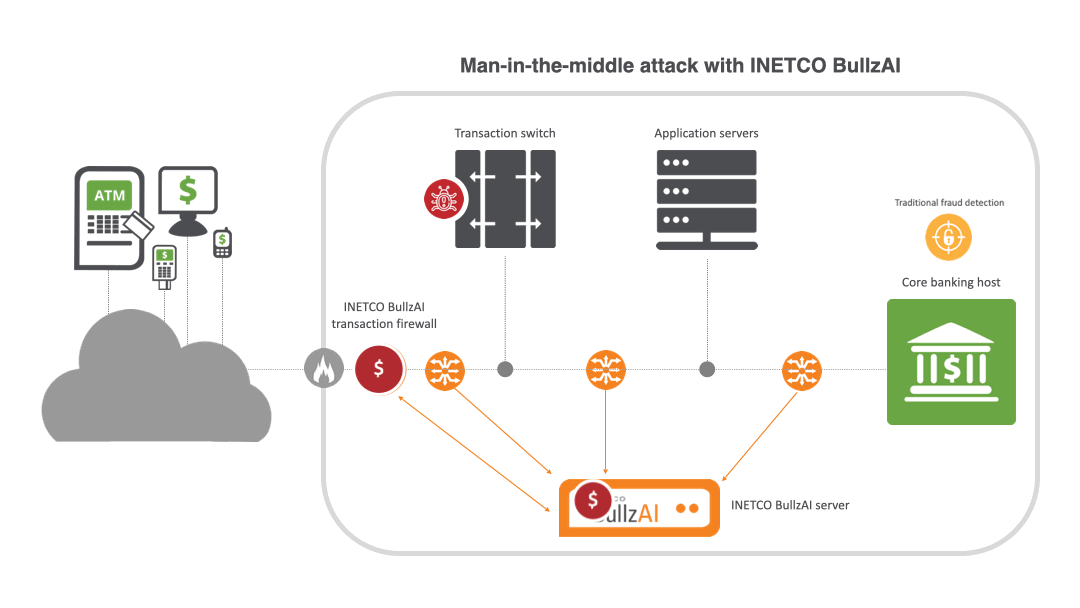
Key capabilities include:
Field-level transaction decoding and end-to-end transaction correlation: INETCO BullzAI captures audit-quality payment data that traditional fraud detection systems often overlook. By examining each individual field within a transaction, it can identify subtle anomalies, such as when a decline response is altered to appear as an approval. It can also identify when a link is missing in a predictable chain of transaction request and response messages, as this is an indicator of traffic interception and a potential malware attack vector.
User and entity behavioral analysis: Utilizing self-learning machine models, INETCO BullzAI analyzes the behaviors of every individual card, user, terminal and device. When a transaction deviates from expected behavior — such as when there is a high amount of stand-in mode approvals, geolocation mismatches or device/IP inconsistencies — it immediately flags and blocks the suspicious activity.
AI-powered transaction firewall: INETCO BullzAI’s patented transaction firewall inspects transaction data at a field level, not just by IP or port. By using machine learning to adapt to new attack patterns, it can evaluate, rate-limit or block transactions based on detailed attributes like terminal IDs, machine fingerprints, and transaction types. This targeted approach increases detection accuracy while minimizing false positives.
The right tech at the right time
As advanced malware and MITM attacks become more common, proactive detection is critical. INETCO BullzAI not only identifies fraudulent transactions, but stops them before they are processed.
Learn more about how the INETCO BullzAI transaction firewall can help you prevent MITM attacks before they impact your customers. Watch the 3-minute video.

