Picture this: It’s a busy weekday afternoon and your online payment platform is humming with activity. Suddenly, everything slows down. Customers complain that transactions are failing, your website goes offline, and your team scrambles to figure out what’s happening. The culprit? A Distributed Denial of Service (DDoS) attack.
Inside a DDoS attack: How they work and why they hurt
These coordinated assaults overwhelm a target’s digital infrastructure with massive volumes of malicious traffic, effectively denying access to legitimate users. Unlike a standard Denial of Service (DoS) attack, which comes from a single source, DDoS attacks leverage networks of compromised devices, known as botnets, to bombard servers, applications, or application programming interfaces (APIs) with anywhere from thousands to hundreds of millions of requests per second.
DDoS attacks are no longer isolated events targeting a handful of businesses. They have become a preferred weapon for cybercriminals looking to extort companies, damage reputations, distract cybersecurity teams from other attacks, or simply create chaos. What makes them especially dangerous is how easy they are to launch, and how devastating they can be for unprepared organizations. The attacks come in various forms, including:
Volumetric attacks: The most common type of DDoS attack floods networks with bogus traffic.
Protocol attacks: These exploit vulnerabilities in layers 3 and 4 of the Open Systems Interconnection (OSI) model to exhaust server resources.
Application-layer attacks: These target business applications and APIs by infecting client devices with malware and then mimicking legitimate user behavior, making them difficult to detect.
Ransomware attacks: Attackers threaten prolonged disruption unless paid a ransom, often in cryptocurrency.
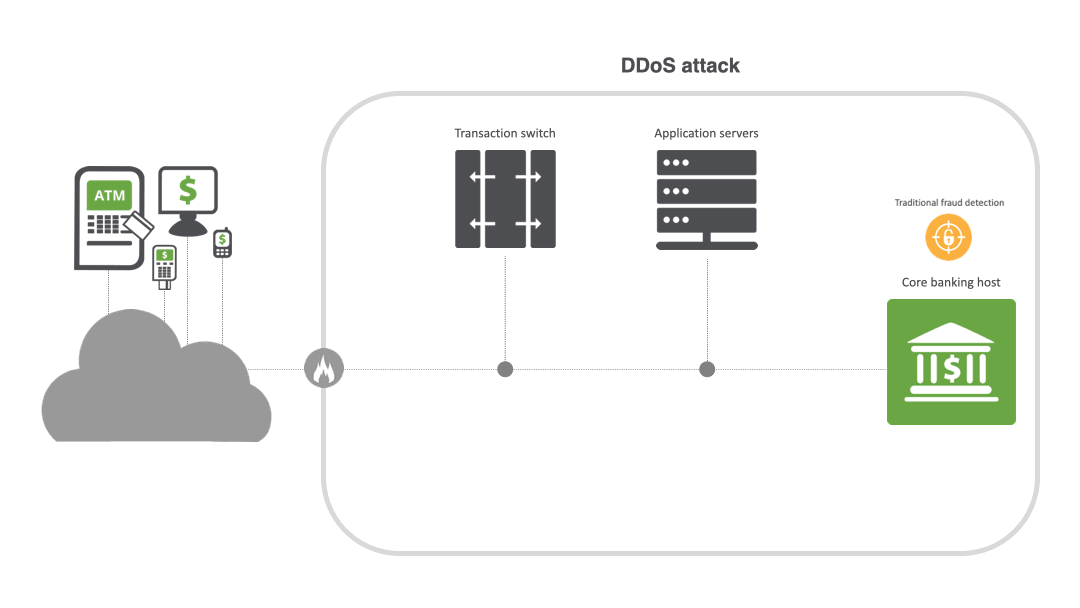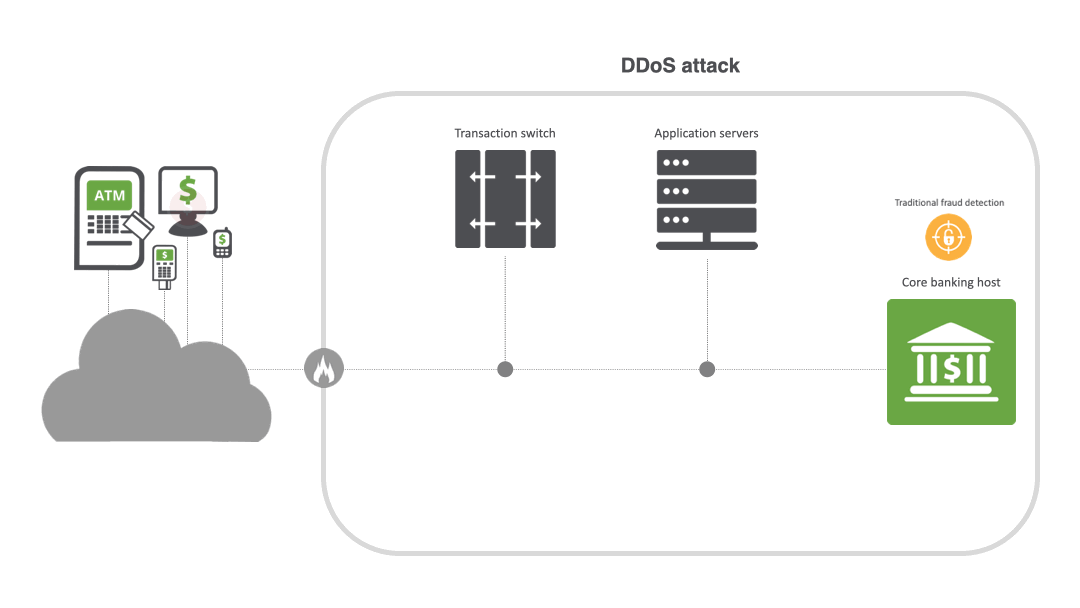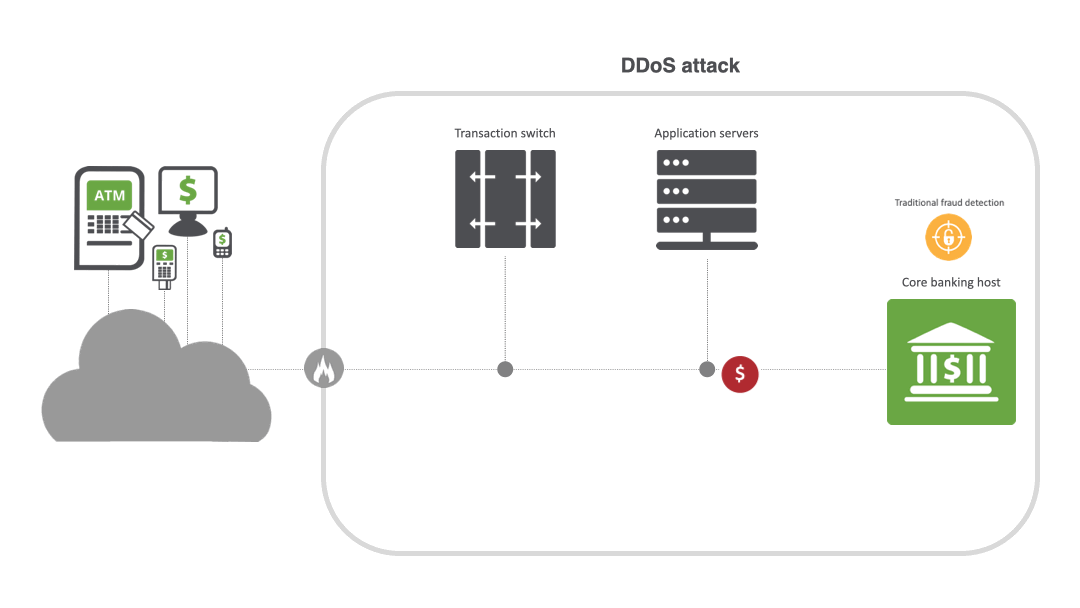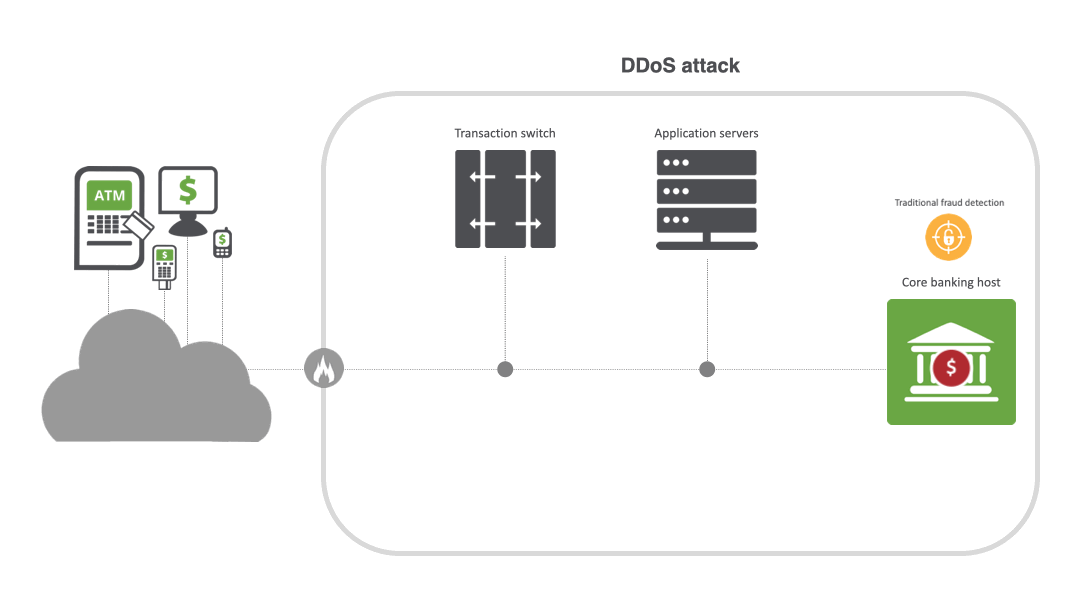
From disruption to destruction: the escalation of DDoS
Let’s look at the major trends shaping today’s more destructive DDoS landscape, defined by longer, larger, more complex campaigns driven by cheap attack services, adaptive AI bots, and rising ideological motives.
Increased length, volume and intensity: A potent mix of geopolitical conflict and technological advancement has supercharged DDoS campaigns. The average length of attacks surged by more than 400 percent over the course of 2023 — from 24 to 121 minutes — while the volume of attacks in the first half of the year jumped 200 percent compared to all of 2022.
Recent examples demonstrate how attack intensity is increasing with each passing week. In October 2023, a new vulnerability in the HTTP/2 protocol led to what was then the largest DDoS attack recorded: A 201 million packets per second (pps) incident, which was soon surpassed by a 398 million pps attack reported by Google. In August of 2024, Global Secure Layer reported a record-breaking packet-based DDoS attack, which reached 3.15 billion pps, primarily targeting unofficial Minecraft gaming servers.
Another record-breaking multibillion-packet attack took place on Sept. 2, 2025, through a massive flood lasting just 35 seconds. Peaking at 5.1 billion pps, the traffic originated from a mix of compromised IoT devices and multiple cloud providers, not solely Google Cloud as initially thought.
Less than three weeks later, Cloudflare shared on X that it had “blocked hyper-volumetric DDoS attacks twice as large as anything seen on the Internet before.” The 40-second incident reportedly peaked at 10.6 billion pps, exposing Cloudflare’s defences to 22.2 terabits of data per second.
Use of DDoS-for-hire services: The rise of “DDoS-as-a-Service” platforms has lowered the barrier to entry for criminals. For just a few dollars, attackers can rent a botnet and launch massive assaults. At the same time, the sheer number of vulnerable Internet-connected devices has become a massive attack surface, and artificial intelligence is amplifying attack capabilities, with bots adapting their tactics in real time to evade detection.
Example: In May 2025, Europol dismantled six major DDoS-for-hire platforms, arrested several administrators, and seized associated domains. Some services offered attacks for as little as $10 per session.
Multi-vector attacks: Modern DDoS campaigns rarely rely on a single technique. Instead, they combine volumetric floods (like UDP or SYN floods) with more sophisticated application-layer (Layer 7) strikes, overwhelming both network bandwidth and server resources simultaneously.
Example: A 2024 Cloudflare report noted widespread multi-vector campaigns combining SYN floods, DNS amplification, and UDP floods, demonstrating how attackers flood different layers at once to overwhelm defenses.
Ideologically motivated attacks: Hacktivism is re-emerging as a driver of DDoS campaigns, particularly targeting financial institutions, critical infrastructure, and governments aligned with controversial geopolitical stances.
Example: In 2023, DDoS attacks on financial institutions rose by 154%, with much of the increase attributed to politically motivated campaigns targeting companies aligned with specific geopolitical issues.
Layer 7 attacks: Application-layer (Layer 7) attacks specifically target web applications, APIs, and portal login pages, exploiting resource-heavy functions like search queries or account validation to exhaust backend systems.
Example: In April 2025, attackers targeted the payment processing API of Adyen, a leading global payments platform, during peak business hours in Europe. Hackers launched an HTTPS flood disguised as real payment requests, obstructing backend services and disrupting transactions across multiple countries.
The true cost of DDoS attacks
With Zayo Group reporting that the average DDoS attack lasts 68 minutes, and with unprotected organizations shelling out an average of $6,000 per minute of each attack, the average cost to businesses adds up to a startling $408,000.
But the damage extends beyond revenue loss. For one thing, reputation damage erodes customer trust after even minor disruptions. For another, operational strain diverts IT teams away from critical work.
High-profile DDoS attacks that shaped cybersecurity
2024 — Google gouged: Peaking at a staggering 398 million requests per second, this August attack “generated more requests than the total number of article views reported by Wikipedia during the entire month of September 2023,” Google reported.
2020 — AWS attacked: The servers of Amazon Web Services (AWS), which provide cloud services for millions of businesses and governments, were hit by an overwhelming 2.3 terabits of data every second. At the time, this was the largest DDoS attack ever recorded.
2016 — Dyn decimated: When this company that manages website addresses was hit by the Mirai botnet, which was made up of hacked smart devices like security cameras, TVs, and printers, the flood of fake traffic knocked out major websites, including Netflix, Amazon, PayPal, Visa, and The New York Times.
Building proactive strategies to beat DDoS attacks
Stopping DDoS attacks in their tracks requires a layered defense strategy involving:
- Continuous monitoring for full visibility into network traffic at both the packet and transaction level.
- Adaptive mitigation techniques that dynamically employ features such as traffic filtering, rate limiting, and the blocking of malicious traffic. This ensures that legitimate users experience uninterrupted access to services.
- Behavioral analytics and AI to establish normal patterns and identify anomalies in real time.
- Surgical mitigation to block malicious traffic at the field level rather than entire IP ranges.
- Cloud-based mitigation and geographically distributed networks that can absorb high-volume attacks.
- Incident response planning with clear playbooks and communication protocols that leverage third-party partnerships.
How INETCO BullzAI neutralizes DDoS attacks
Unlike traditional web application firewalls (WAFs) or fraud solutions, INETCO BullzAI inspects every transaction in real time to detect anomalies and provide AI-powered protection against sophisticated multi-vector DDoS attacks, particularly at the application layer. Its patented transaction firewall inspects encrypted transaction data at the field level and enforces rules to detect and rate limit or block DDoS attacks in milliseconds — not hours or days — while ensuring that legitimate transactions can go through.
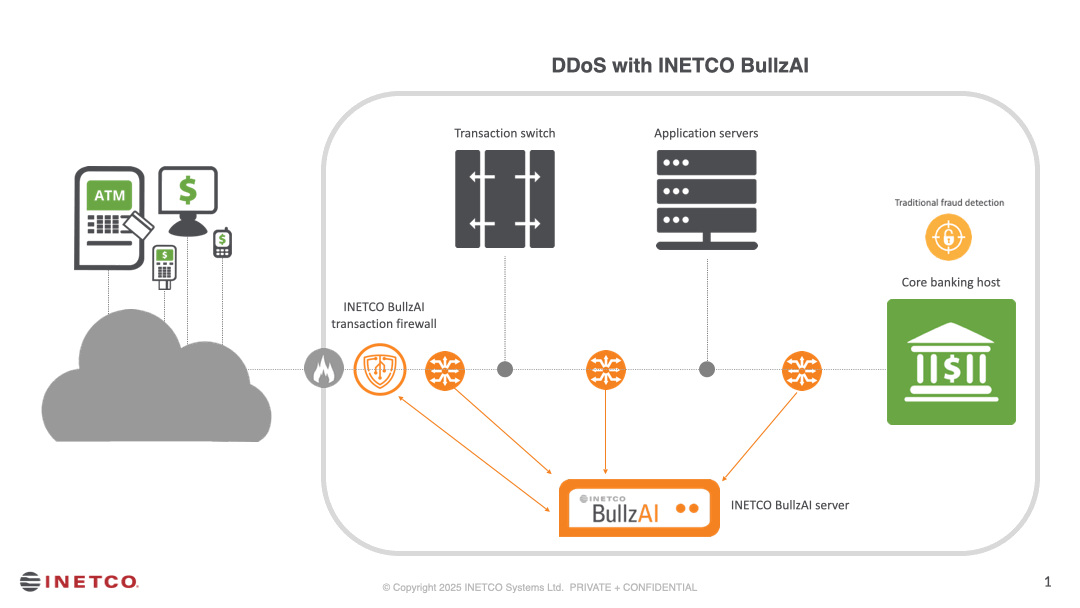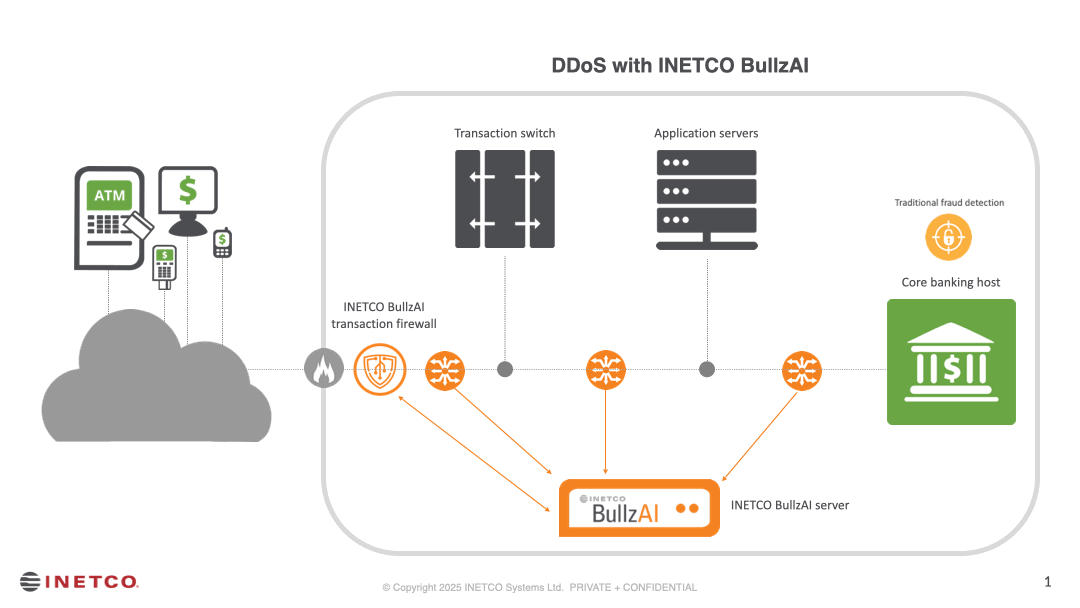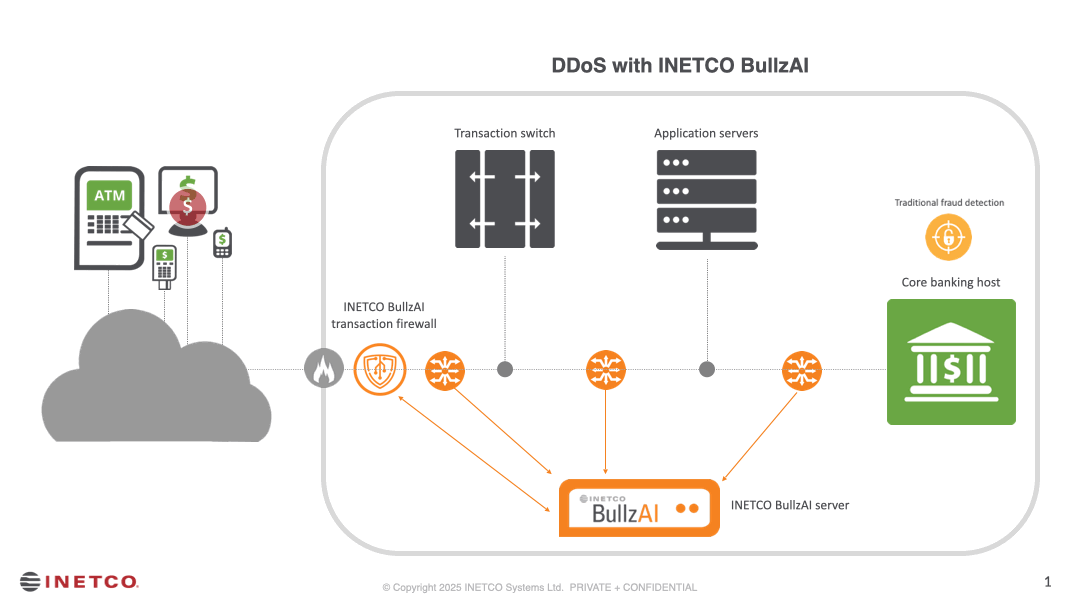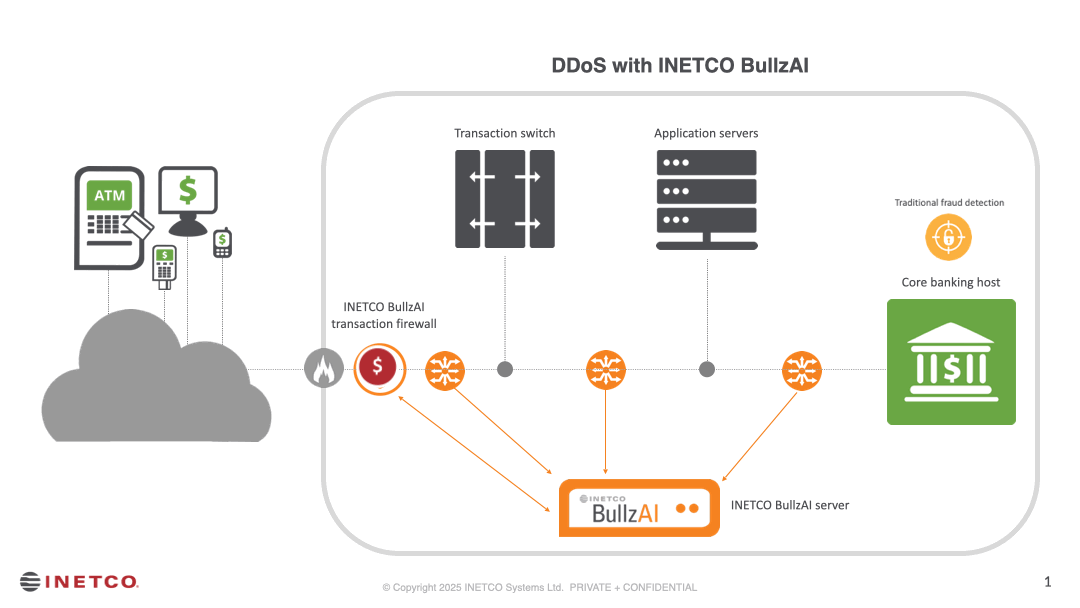
This proactive approach ensures businesses can:
DETECT
- Instantly identify high-velocity transaction spikes, fake account creation, or floods of activity from the same true IP address.
- Examine every data field across the end-to-end transaction journey for anomalies and encoded signals other solutions miss.
PREVENT
- Rely on self-learning AI models and adaptive risk scoring to build predictive intelligence.
- Spot unusual behavior patterns across cards, devices, terminals, applications, and accounts.
- Anticipate evolving DDoS attack vectors with continuous real-time analysis that eliminates blind spots.
- DDoS attacks are often launched to distract teams while another cyberattack is launched. With INETCO BullzAI’s real-time detection and blocking ability, other anomalies can be detected and prevented. It’s like having an extra resource on your cybersecurity team.
SHIELD
- Block DDoS attacks in milliseconds by inspecting every transaction data field, including true IP geolocation.
- Target malicious sources at the device, account, or application level — not just at the “widespread” IP or port level.
- Preserve legitimate transactions and customer trust while keeping business services uninterrupted.
DDoS attacks have evolved from nuisances into strategic weapons that can cripple even the most prepared organizations. As incidents grow in scale and sophistication, outdated defenses no longer suffice. With INETCO BullzAI, businesses can protect their networks without frustrating legitimate customers, while also reducing downtime, and safeguarding revenue.
Learn more about how the INETCO BullzAI transaction firewall can help you prevent DDoS attacks before they impact your customers. Watch the 3-minute video.

