You just started reading this blog post. But are you reading it alone? Or is there a “man in the middle” watching and recording everything you do online? While it may sound like a plot from a Hollywood blockbuster, the reality is far from amusing.
A man-in-the-middle attack (MitM attack) can quickly occur when an unsuspecting victim joins the same public Wi-Fi network as a malicious attacker, for example, at a cafe. Once the victim joins the network, it only takes a few steps to compromise that device completely. If they work remotely, threat actors can use this device to penetrate enterprise networks. It also gets more complex and challenging in industries like finance and banking.
What is a Man-In-The-Middle Attack?
A man-in-the-middle attack is a type of cyberattack where threat actors lurk in the shadows eavesdropping on conversations between a network user and a web application. This approach helps hackers exploit real-time processing transactions and the transfer of sensitive data.
MitM is an umbrella term for different types of cyberattacks, including:
- ARP spoofing
- DNS spoofing
- Email hijacking
- HTTPS spoofing
- IP spoofing
- Stealing browser cookies
- SSL hijacking
- Wi-Fi eavesdropping
The primary objective of man-in-the-middle attacks is to surreptitiously collect sensitive data like usernames, passwords, banking details, and more. Criminals can use this information to impersonate the victim and solicit additional information, social engineering attacks, identity theft, and fraud.
MitM attacks are widespread in the financial industry. By breaching a bank or payment card processor, criminals can manipulate fraud detection controls, modify customer accounts to intercept emails with bank details, and initiate ATM cash-out and jackpotting attacks.
For example, in a MitM attack for ATM cash-outs, malware is placed on the transaction switch, enabling the creation of cloned cards distributed to money mules. Once the switch is compromised, and the malware is activated, the transaction switch goes into a stand-in mode and starts to approve the fraudulent transactions across a large number of ATMs.
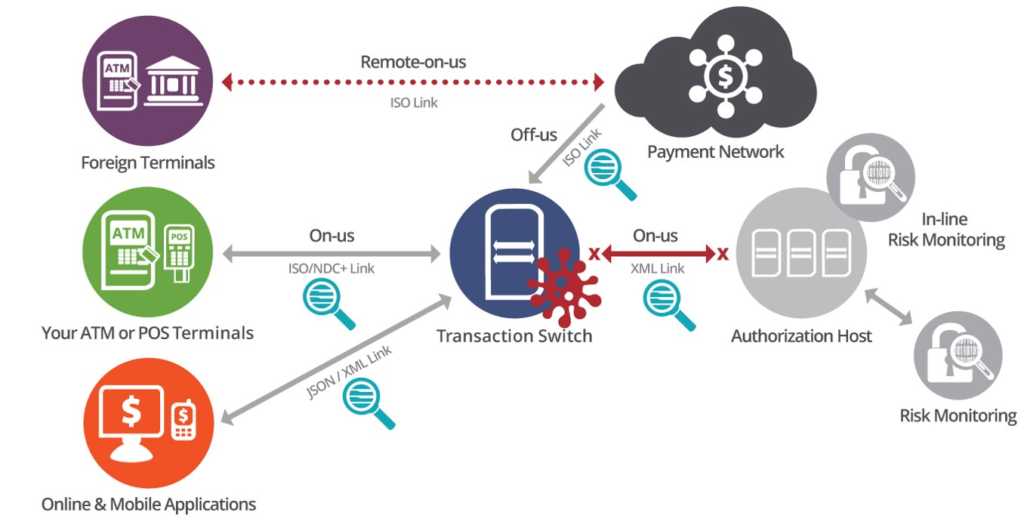
Threat actors can also silently intercept information sent between two parties and reroute it to phishing sites. They can also easily encrypt malware in the connection. As malicious actors disguise themselves as the endpoint in a line of communication, it’s challenging to spot them.
Why Have Man-In-The-Middle Attacks Grown Exponentially?
With the disruption brought on by the COVID-19 pandemic in 2020, the number of people who work and shop online increased dramatically. As companies rushed to digitize their operations, it allowed hackers to hide more easily on enterprise networks and execute attacks at will.
Research suggests that financial institutions and merchants must be on high alert in the current threat landscape. According to the Arkose Labs 2021, Q2 Fraud and Abuse Report, the first quarter of this year saw a diversification of attacks across use cases. These include bot-driven API abuse, fake reviews, information scraping, in-game abuse, inventory hoarding, and spam.
There was also a considerable increase in payment-related attacks (up by 27.6% compared to the fourth quarter of 2020) and a 36.1% increase in abuse and spam. Attacks on logins continued to remain high at 45% of all attacks.
According to a Web Arx Security report, 300,000 thousand new pieces of malware are created every day. These are designed to steal data and include spyware, adware, Trojans, and viruses. In 2020, ransomware cost businesses a total of $20 billion.
How Do You Prevent Man-In-The-Middle Attacks?
Prevention starts with awareness. With the right tools and expertise, you can mitigate risk and keep your brand name out of the headlines. But how do you do it?
Leverage Authentication Tools
One of the first steps you can take to prevent MitM attacks is to secure your end-to-end communications. This means that you must protect access points through authentication protocols and fortify your defenses with a robust monitoring and detection platform. However, this process should extend far beyond customer-facing applications and be enforced across all internal platforms.
Use Robust Detection Protocols
You need to have control over all your systems to establish rules and alerts to detect any suspicious activity. You must monitor your infrastructure in real-time and enforce security protocols whenever you identify suspicious behavior. This applies to internal networks and where there’s always a potential for insider fraud threats.
Always Use a Virtual Private Network (VPN)
Ask staff to always connect to enterprise networks through a VPN. This approach helps mask IP addresses and encrypt data transmitted over the internet. Although it doesn’t make MITM attacks impossible, it sure does make it harder for threat actors.
Engage in Regular Staff Training
Humans have consistently maintained the top spot as the weakest link in the security chain. To mitigate risk, conduct regular security training workshops to keep your employees aware and alert.
For example, security training will help raise awareness of phishing scams and other social engineering attacks. Employees will also know that they should only visit HTTPS websites that encrypt data, rendering intercepted communications meaningless.
How Can INETCO Help?
A unique capability of INETCO is its ability to detect man-in-the-middle attacks on the transaction switch.
Standard fraud detection solutions sit on the back end of the transaction – on the authorization host – and rely on switch or core banking system data being passed to them so they can perform account verification and enforce transaction limits.
Man-in-the-middle malware forces the transactions switch into a stand-in mode and starts to approve fraudulent transactions. As transactions never go to the back-end to be authorized, the limits on accounts are not enforced and fraud detection systems are blind-sided. With fraud systems unaware, an unlimited number of attacks and withdrawals can happen without ever being detected or stopped.
Only INETCO provides a robust and unique solution that makes spotting man-in-the-middle attacks easy. Through real-time network-based transaction monitoring with multi-link analysis, we can help match a user request to all the various backend calls and services required to execute it.
For example, one of the largest financial institutions in Africa found itself the target of a sophisticated, highly coordinated ATM fraud attack in late 2016. Approximately 100 people used forged credit cards and withdrew a whopping $19 million from 1,400 ATMs in one city within three hours.
This man-in-the-middle attack is identified in real-time by INETCO Insight. INETCO Insight captures, decodes, and correlates every hop of each payment network transaction to immediately flag anomalous network behavior and transaction patterns. It correlates each link in the end-to-end transaction to promptly see if links that should be present in a transaction are missing.
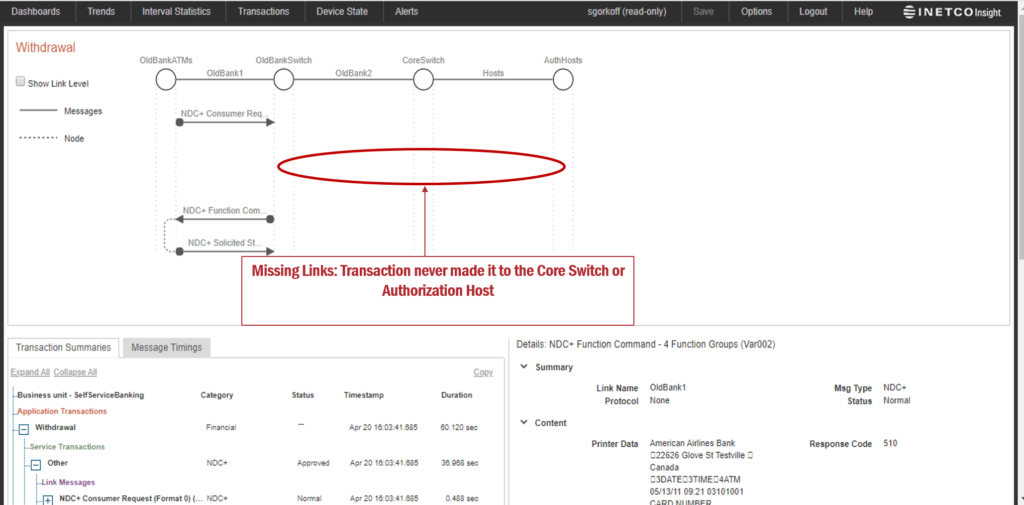
In this scenario, INETCO Insight triggers an alert if the system detects any missing transaction links (backend transactions). This works as one of the most vital indicators of fraud. Missing communication links for approved transactions is also a strong indicator of malware trying to bypass the Authorization Host to approve fraudulent ATM withdrawals.
To learn more, schedule a commitment-free consultation or request a demo.

