Table of Contents
A medical lab scientist landed in Johannesburg on Saturday, February 5th, for his two-week assignment. Soon after landing, family and friends called him to say that some people were calling and texting them, looking for him. Those people were hackers, who had got hold of his contacts. The scientist didn’t pay much attention to it, but two days later he received a message from his telecom company that they had received a SIM card swap request from him, which he, of course, never made.
Between February 7th and 9th, Kenyan Sh2.6 million (more than $22,000 USD) was stolen in several transactions from his four different bank accounts. At first, the scientist couldn’t access his account to check it, but when he finally managed to log in, it was too late to prevent the cybercrime.
This true story is a scary example of a SIM swap – a type of mobile fraud that is an emerging threat not only in Africa but around the world. While mobile fraud is not new, the tools and techniques of stealing funds through mobile phones continue to evolve and now pose a serious threat to mobile users, financial organizations, and businesses.
Mobile Banking Threats on the Rise
In 2022, mobile banking risks are increasing. In Q1 2022, ThreatFabric reported that on-device fraud increased 40% year-over-year. It’s not a surprise, as many of us rely on our devices and the convenience of using them to store personal and financial data for making transactions. 44% of bank customers globally use their bank’s mobile app as their preferred channel. In the USA that number reaches 87%.
Nokia’s 2021 Threat Intelligence Report announced that the number of new banking trojans observed in global mobile networks increased 80% year-over-year in the first half of 2021. While these trojans were significantly active in Latin America and Europe, their prevalence expanded to other regions. Banking malware mainly targeted Android devices to steal personal banking credentials, credit card information, and one-time passwords, due to the accessibility of the Android development platform.
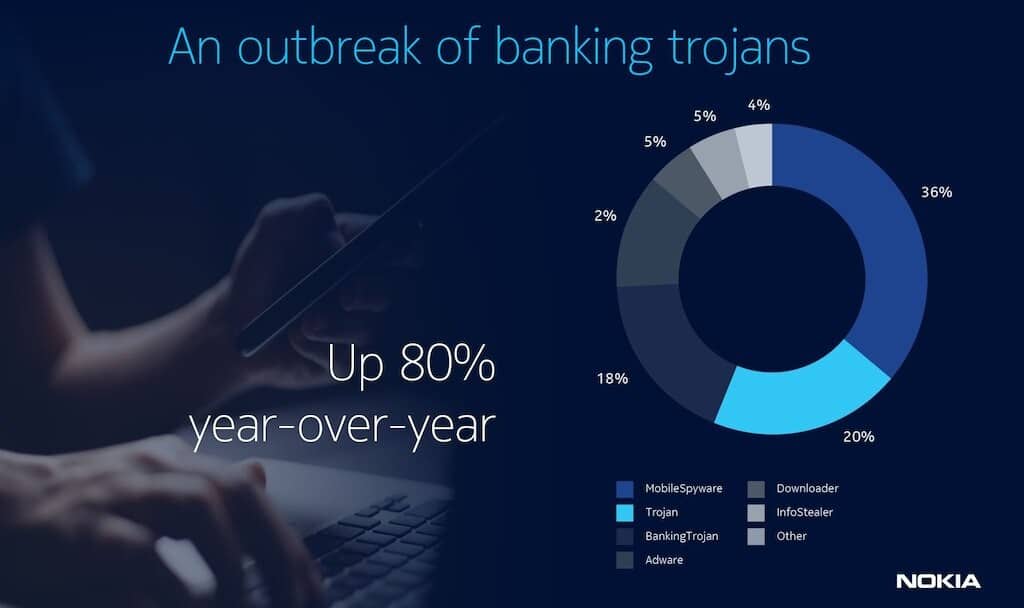
Android trojan has hit over 10 million mobile users globally. This aggressive mobile premium services campaign was a tool to steal hundreds of millions of euros. The GriftHorse trojan took advantage of user interactions for increased spread and infection.
5 Most Common Types of Mobile Fraud
Here are a few mobile fraud types that we observe the most often:
1. SIM Swapping
Fraudsters persuade the mobile operator to do a SIM swap with a new SIM card that they then use to access user accounts and use one-time passcodes. Alternatively, fraudsters can use card copying software to clone the victim’s SIM card and create its duplicate to gain access to their phone calls and messages. Then they can make purchases or transfer funds on the victim’s behalf.
2. Mobile banking malware
As described in the Nokia’s report, banking malware threats have risen with the popularity of mobile banking on smartphones. To collect users’ information, banking trojans use keystroke capture, bank login screen overlays, and screen snapshots.
Once a banking trojan is on the phone, it remains in the background collecting the data the fraudsters need, so prevention is key for protecting your business: education campaigns on cybersecurity for your customers will play a big part. Learn more about our digital & mobile banking solutions.
3. Device cloning
The amount of personal data we store on our mobile devices is constantly increasing as we access online stores, bank accounts, and other useful applications. Fraudsters make a replica of the original device and transfer all the data to it, so they are able to make calls and purchases without any device checks, while the owner is billed for the transactions.
4. Reverse Engineering
Fraudsters can reverse engineer an app to analyze its source code and component parts. They can later use that information to deploy their own malicious app (like a fake online banking app) or exploit the vulnerabilities of an existing app.
5. Man-in-the-Middle (MitM) Attack
In cases of the MitM attack, the fraudster intercepts network traffic between the financial institution and the customer. For example, a bad actor can set up a malicious Wi-Fi network that will transfer the customer’s payment data to them once the customer accesses the hotspot.
How To Protect Your Business and Your Customers
The best practices of mobile fraud prevention globally usually include customer education campaigns on cybersecurity.
As good as these campaigns might be, protecting your customers against cybercrime and financial loss cannot be left entirely to them. Many will ignore best practices in favor of frictionless transactions, no matter how much you invest in education.
When sophisticated fraudsters steal credentials and get past authentication systems their fraudulent transactions can still be detected and blocked before customers suffer financial loss.
INETCO BullzAI’s next generation entity and user behavioral analytics (EUBA) build a unique behavioral profile for every customer, card and device, enabling it to detect anomalous transactions in real-time, based on an individual’s unique transaction history. When a fraudster imitates a customer, INETCO BullzAI detects such details as a new IP address, new device ID, transfers to previously unseen email addresses, bank accounts and delivery addresses, high-velocity transactions, unusual transaction amounts, and many more. The analysis is performed in real-time enabling transactions on any channel to be blocked before they complete.
INETCO BullzAI for payment fraud prevention is also uniquely positioned to detect and block man-in-the-middle attacks. It captures, decodes, and correlates every hop of each payment network transaction to immediately flag anomalous network behavior and transaction patterns. It correlates each link in the end-to-end transaction to promptly see if links that should be present in a transaction are missing.
Despite the speed with which criminals evolve new methods to commit cybercrimes, it’s possible to be faster than fraudsters if you use the right strategies and tools to protect your critical infrastructure, resources and customers.
Need help to improve your mobile fraud prevention and overall cybersecurity strategy? Get in touch with one of our experts.

