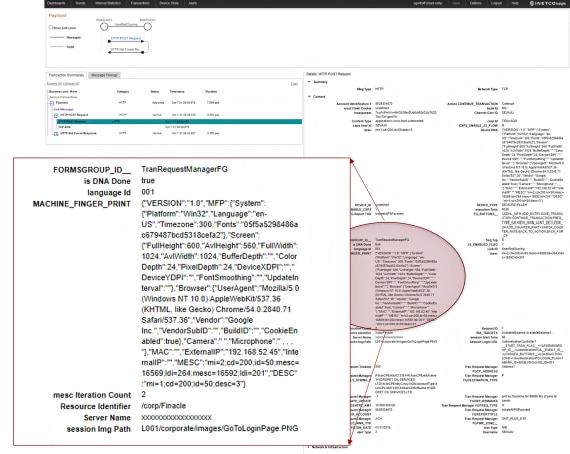
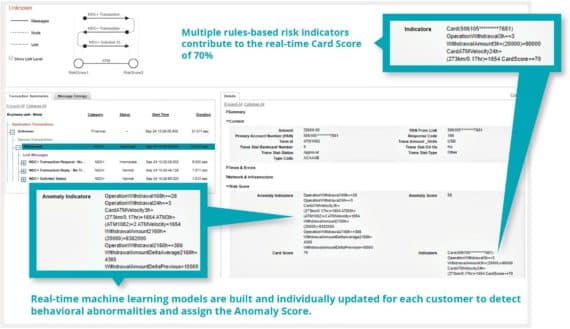
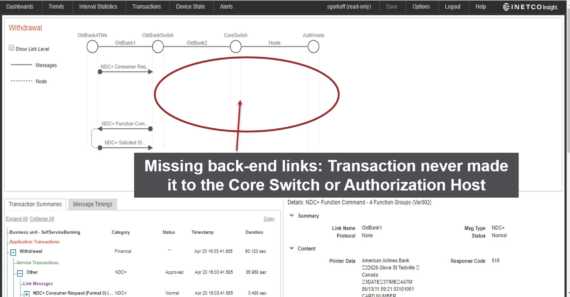
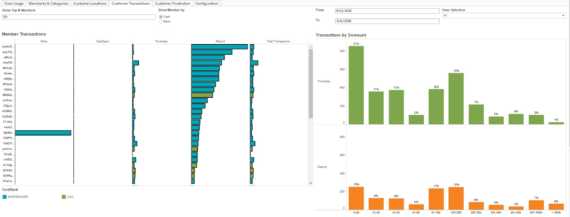
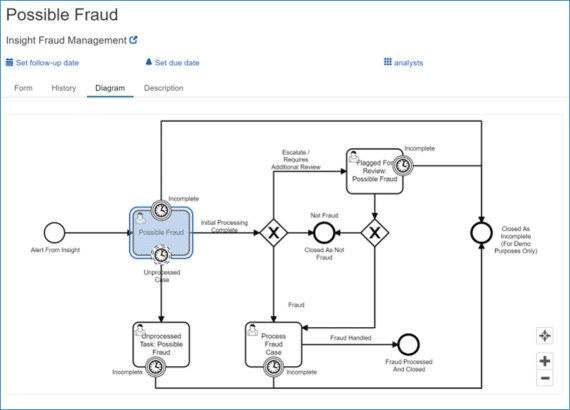
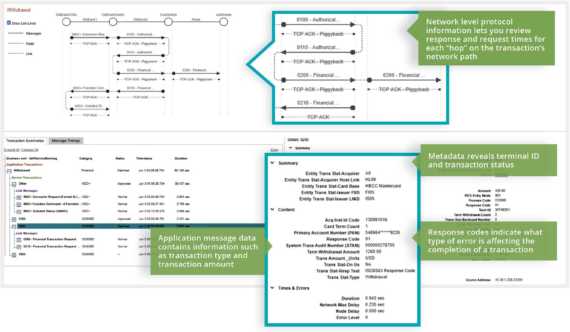
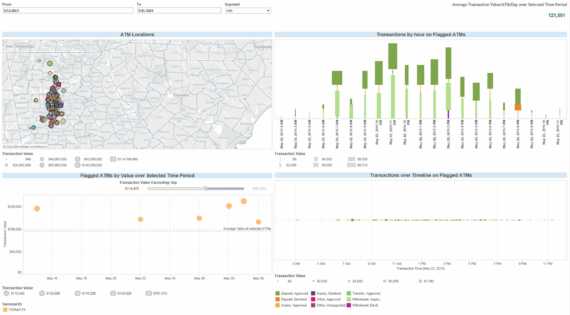
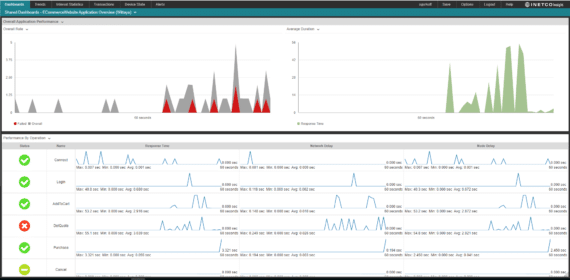
Helping payment fraud and real-time cybersecurity monitoring teams increase fraud coverage and accurately detect suspicious transaction-level activity in milliseconds – without breaking the budget
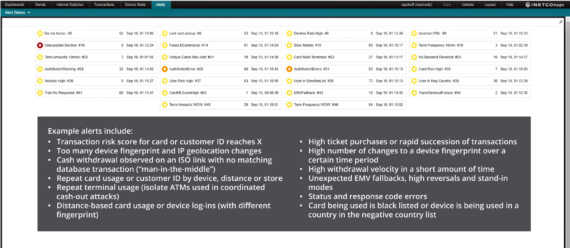
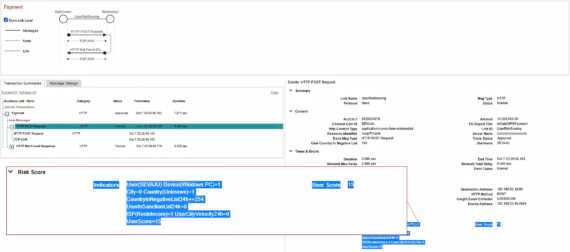
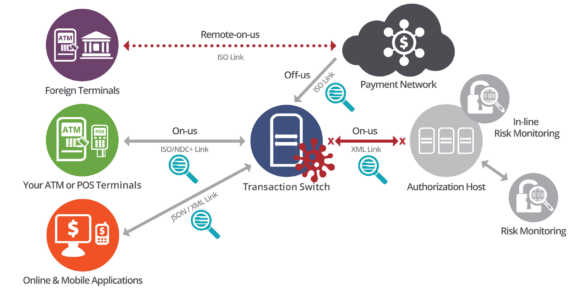
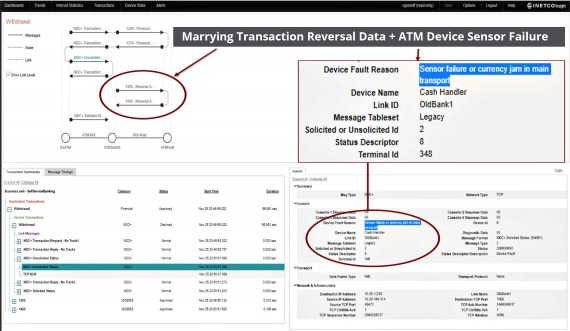
The recent surge in digital transaction volumes has paralleled an increase in self-service and cybersecurity attacks which is forcing businesses to revisit their security monitoring strategies and cyber defenses. To win customer trust and minimize financial loss, you must take steps to reducing onerous false positives and make sure every transaction is secure. This means it is time to increase the speed, coverage and precision of payment fraud detection and prevention – across all channels.
The authentication or the decline of a payment transaction is often the defining factor of the end-customer experience. This is why there has never been a better time for payment fraud and cybersecurity teams to layer their omnichannel fraud detection and prevention strategies with INETCO Insight. Maintain the highest security standards, and avoid detection lag times. Leverage insightful, real-time data to improve the customer experience thanks to security threat monitoring.