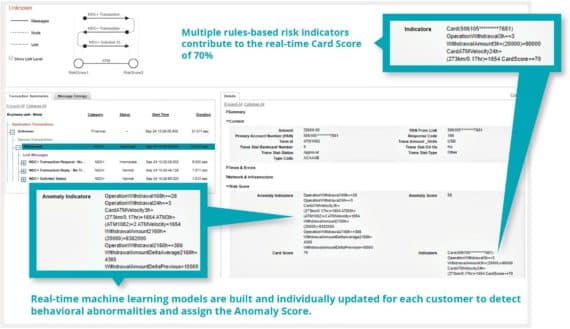
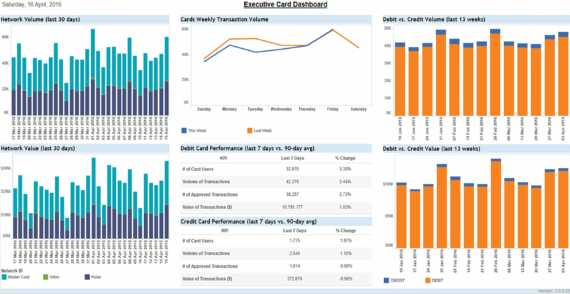
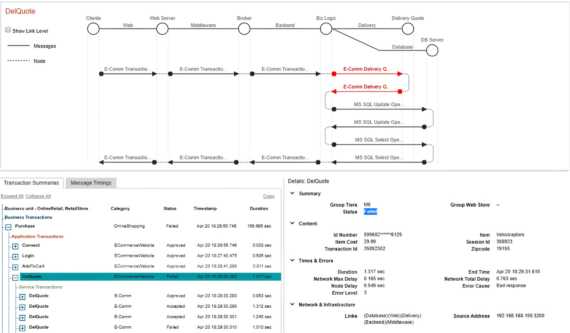
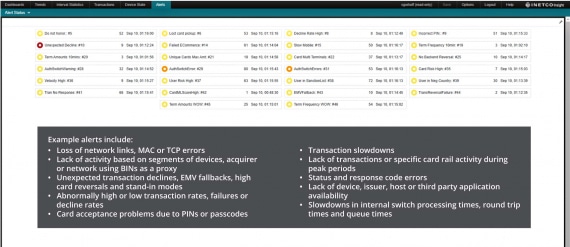
Helping card operations teams increase the value, safety and stability of every card transaction
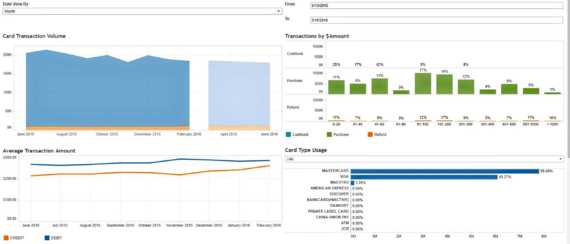
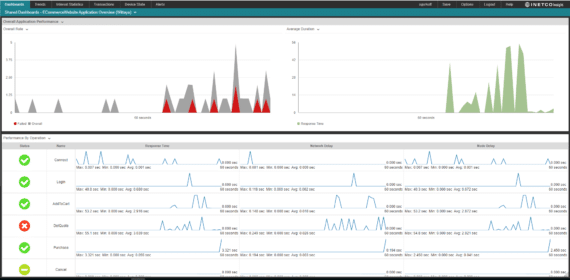
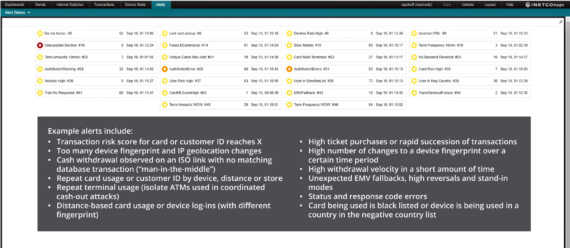
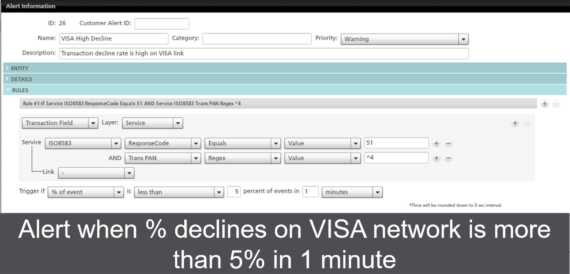
The payment card business is currently under a lot of strain, as card operations teams face the difficult job of balancing amazing customer service with revenue concerns. Keeping a customer engagement strategy successful and profitable requires constant analysis of shifting consumer buying behaviors. Delivering stable card rails and adopting a payment security strategy that keeps you ahead of the fraudsters exploiting the surge in digital transactions will have a positive impact, as well.
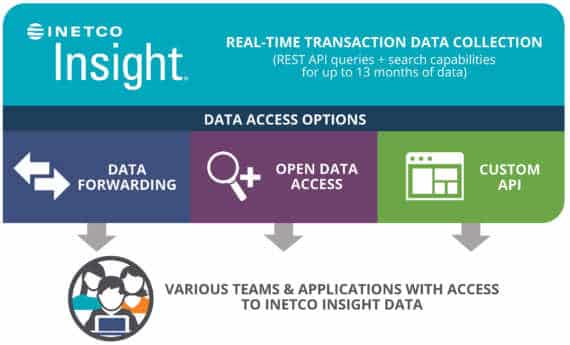
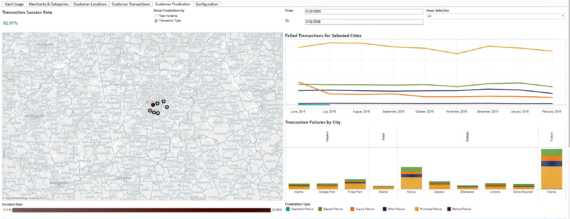
This is where INETCO Insight helps.